5.1. FIRST CSIRT services framework
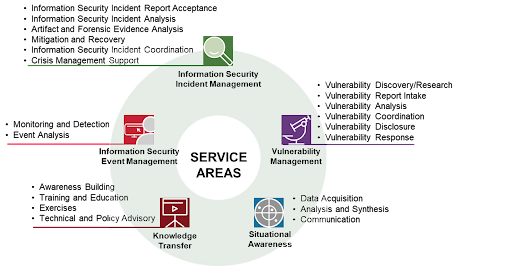
The FIRST CSIRT Services Framework categorises CSIRT services into five service areas, each area having several services. Most CSIRTs offer incident response services. The CSIRT cases can be classified based on the category, criticality level, and sensitivity level. The five service areas are:
- Information Security Event Management (ISEM)
- Information Security Incident Management (ISIM)
- Vulnerability Management (VM)
- Situational Awareness (SA)
- Knowledge Transfer (KT)
5.1.1. Information Security Event Management (ISEM)
This service area identifies information security incidents based on the correlation and analysis of security events from a wide variety of event and contextual data sources’’. ISEM service offerings include monitoring and detection, along with event analysis. Using automated, continuous processing tools, the CSIRT extracts data from a wide variety of information security event sources and contextual data, in order to identify potential information security incidents. Event analysis involves grouping and correlating events to qualify them as potential information security incidents for escalation to the Information Security Incident Management service area, or as a false alarm.
Based on the National Initiative for Cybersecurity Education (NICE) Workforce Framework for Cybersecurity, the CSIRT should have competencies in data management, infrastructure design, network management, and operating systems to deliver the monitoring and detection service. Skills required to deliver the event analysis service are incident management, data analysis, threat analysis, computer forensics, and cyber threat monitoring. Training and certification in those areas are provided by SANS, Udemy, EC-Council, IBM, AfricaCERT, ENISA, FIRST, CIRCL, CERT-Tools Community, ICANN, and CREST.
5.1.2. Information Security Incident Management (ISIM)
This is the main service that a CSIRT provides to its constituents. The team collects, evaluates, and analyses information security incident reports. The results of the analysis are used in recommendations given to constituents for the mitigation of, and recovery from the incidents. This service requires the CSIRT to coordinate with other CSIRTs, or security experts to ensure that all aspects of the incident are addressed and to help reduce similar future attacks.
Various frameworks and guidelines provide guidance on CSIRT services including the Computer Security Incident Handling Guide. This guide provides guidelines on the creation of an incident response policy and plan, developing procedures for performing incident handling and reporting, setting communication guidelines, selecting a team structure and staffing model, establishing relationships and lines of communication between both internal and external parties, and determining which services the incident response team should provide. Others include the Carnegie Mellon University Engineering Institute (CMU-SEI) and RFC-2350.
The core competencies required in the ISIM area include computer forensics, data analysis, incident management, threat analysis, vulnerability assessment, information systems/network security, system testing, evaluation and administration, encryption and soft skills including critical thinking, written and oral communication, client relationship management, conflict and knowledge management. The team requires competencies in law, regulations, policies, and ethics.
Training identified for this service area includes, but is not limited, to those offered by SANS – Hacker Tools, Techniques, and Incident Handling, CMU-SEI- CERT Incident Response Process Professional Certificate, EC-Council – Certified Incident Handler Program, Udemy – Cyber Security Incident Handling and Response, Cyber Security Incident Response and Mile2- C)IHE Certified Incident Handling Engineer course.
5.1.3. Vulnerability Management (VM)
The Vulnerability Management Service Area includes services related to the discovery/research, analysis, and handling of new or reported security vulnerabilities, including coordination, disclosure, and response. In this service area, CSIRTs offer services that establish a continuous process of identifying, analysing, disseminating, and remediating vulnerabilities in information systems.
Guidelines for the provision of this service are contained in ISO/IEC 29147:2018 Information Technology – Security Techniques – Vulnerability disclosure, ISO/IEC 30111:2019 Information technology – Security techniques – Vulnerability handling, the FIRST Product Security Incident Response Team (PSIRT) Services Framework and the Dutch National Cybersecurity Center Coordinated Vulnerability Disclosure: the Guideline.
To offer this service, a team requires competencies in vulnerability assessment, threat analysis, computer languages, operating systems, web technology, network management, system administration, software testing and evaluation, data privacy and protection, encryption, information assurance, identity management, asset/inventory management, database administration including soft skills such as critical thinking, conflict management, oral and written communication, as well as knowledge and client relationship management.
Training and certification in these areas include, but are not limited to SANS, CREST, Offensive Security, EC-Council, CompTIA, MILE2, and Udemy.
Case Study: Log4shell or Log4j vulnerability
Log4shell is a critical vulnerability in the widely-used logging tool Log4j. The UK National Cybersecurity Centre published information on “Log4j vulnerability – what everyone needs to know“, including tips for organisations that had been affected.
On 13 December 2021, the EU CSIRTs Network escalated to Alert Cooperation Mode’’ on the Log4j. The CSIRT’s Network Members exchanged information, contributed to updating the list of vulnerable software, published relevant advisories for the benefit of their constituencies, and met to discuss the results of two reporting surveys and national situations from 10 to 12 December 2021.
On 12 January 2022, based on the data collected, the national reporting, along with the absence of large-scale or cross-border incidents, the EU CSIRTs Network decided to move back to default cooperation mode, in relation to the log4j/log4shell vulnerability.
5.1.4. Situational Awareness (SA)
Situational Awareness comprises the ability to identify, process, comprehend and communicate the current state and anticipated potential changes in a CSIRT’s area of jurisdiction. This service requires the team to gather, integrate, and disseminate information to its constituents to enable them to make informed decisions. The information is made available for the delivery of other services, including Security Event Management, Incident Management, and Knowledge Transfer.
The service offerings in this area include data acquisition, analysis and synthesis and communication. In order to deliver this service to its constituencies, the CSIRT requires competencies in asset/inventory management, enterprise architecture, systems integration, threat analysis, vulnerability assessment, data analysis and management, modelling and simulation, data and privacy protection, information assurance, identity management, encryption and soft skills in oral and written communication, knowledge and client relationship management, organisational and technology awareness.
5.1.5. Knowledge Transfer (KT)
Given the unique position of the CSIRT’s service, the team collects, analyses, identifies security threats, trends, and risks, and develops operational practises to assist its organisations in detecting, preventing and responding to incidents. The transfer of this knowledge through awareness building, training and education, exercises, technical and policy advisory services to the constituents, is crucial to improving overall cybersecurity.
The competencies required for this service are oral and written communication, interpersonal skills, knowledge management, presenting effectively, workforce management, strategic management, teaching others, client relationship management, business continuity, conflict and risk management.
Training in this area is available from CREST, MITRE, SANS– Security Strategic Planning, Policy, and Leadership, A Practical Introduction to Cyber Security Risk Management, NIST- links are for free and low-cost online educational content, ESET, NINJIO – Cybersecurity Awareness Training, KnowBe4 – Security Awareness, and CybSafe – security awareness training.

Indeed resourceful