9. Process for developing legislation and regulation part 2 (policy to regulation)
We discussed the transition from strategy objectives to policy in the previous sections. We also mentioned various areas that would be best addressed by legislation and others that the use of regulation may be better leveraged to address implementation. This section will provide an overview of how policy directions can be transformed into regulations.
The technical task for officials producing regulation is to convert policy aims and ideas into a detailed set of rules and processes. These rules and processes should be geared to achieve the goals that the policy direction has proposed. The primary issue at the beginning is determining the regulatory approach that best addresses the policy objective. This is because there is a need to strike a balance between using regulation to control and restrict unacceptable activities in cyberspace, while not preventing the vast advantages derived from it.
When considering regulation, an early decision is the type of regulatory approach that will be followed. There is a range of options from heavy-touch to light-touch. The heavy-touch approach is best suited for issues that require restrictions in order to prevent damage or destruction. The light touch approach can be used where guidance is needed to attain a particular objective. Below is a diagram that depicts the spectrum of regulatory options from heavy-touch to light-touch.
.
While there are no specific regulatory processes designed for cybersecurity regulations, various generic regulatory processes can be adapted for use in cybersecurity regulations. A good example is the UK NAO’s ‘Good practice guidance: Principles of effective regulation’. This practice guidance recommends applying the following regulation development lifecycle to cybersecurity regulation.
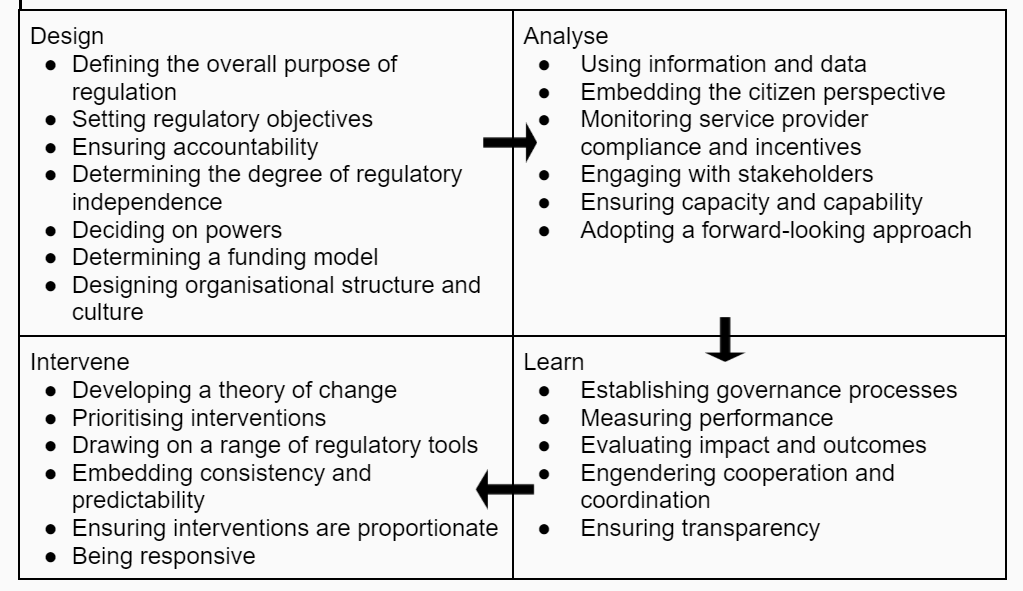
When developing regulation the government will consider what architecture is needed to oversee, maintain and enforce the regulation. Sometimes, primary legislation may make provisions on how the regulations made by a particular body should be implemented, thus recommending the architecture for such regulations. Typical levels in the architecture may include:
- Body(ies) to oversee the regulatory framework and monitor its implementation;
- Body(ies) to develop regulations on particular or several issues;
- Body(ies) to enforce or administer the regulation;
- The entities that are being regulated and need to follow the regulation; and
- The consumer or citizen or beneficiary who is protected by the regulation.
Sometimes, new entities may need to be created to implement and enforce a regulation or assign new enforcement power to an existing legal entity.
We should note that considerations for developing regulations should not be restricted to only domestic issues. Officials developing regulations will need to understand the international regulatory landscape for the relevant policy area. Within Africa, the AU Convention on Cyber Security and the Protection of Personal Data (aka Malabo Convention) has provisions relevant to regulating data protection and electronic transactions.
At the international level, there are good practice frameworks for cybersecurity that regulation can make use of, such as NIST and ISO. There are also a large number of national and sectoral regulations that companies must comply with, and governments should take account of when developing their regulation. For example, the EU’s General Data Protection Regulation (GDPR) regulates the protection of data of the EU citizens and applies to organisations that handle that data even if they are outside the EU.
Governments can use regulations in other jurisdictions for ideas in their national regulation. For example, Egypt’s Data Protection Law (Law No. 151 of 2020) contains many provisions similar to the EU’s GDPR. (PWC 2020, 16) When companies have to follow a single process to comply with the regulations of multiple markets, it reduces compliance costs and workload.
Case study
In 2016, the UK decided to use less interventionist policy levers. For example, focusing on educating the boards of companies rather than regulating them. When the UK reviewed their approach in 2022, it concluded that companies were improving their cyber risk management but not quickly enough to meet the changing threat, so it decided to shift towards “a more interventionist approach to utilising market incentives and regulations to quickly establish better practices”. This illustrates how governments can keep their use of policy levers under regular review and change the balance of levers they use. [Source for this case study: (UK Department for Digital, Culture, Media and Sport 2022, section 4)]
