3.2. How to set up CSIRT and SOC
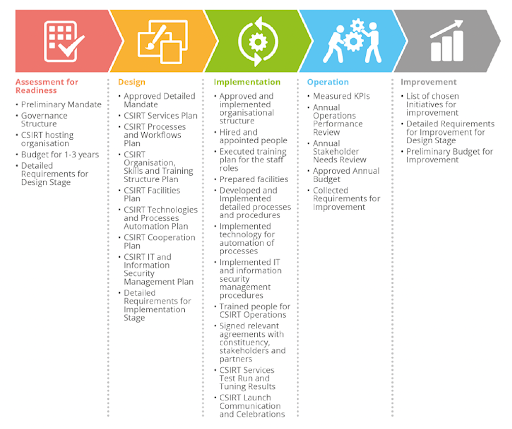
ENISA provides guidelines for setting up CSIRT and SOC that are organised in five (5) phases: assessment for readiness, design, implementation, operations and improvement.
Phase 1: Assessment for readiness – At this phase, the preliminary mandate of authority, the governance structure defining the responsibilities of stakeholders of a national CSIRT and the identification of the CSIRT hosting organization is determined. These elements are usually expressed through a law, a cybersecurity strategy, or a cybersecurity plan.
Good practice: Well thought of organisational positioning
The national CSIRT should be positioned to take advantage of the nation’s organisational structure, i.e. established in law, connected to the national crisis management structure, and available as an international point of contact for cybersecurity incidents.
This phase includes the consideration and approval of a high-level roadmap and budget that includes the expected timeline for the CSIRT establishment phases and the detailed requirements for the design stage.
Good practice: Establish the right mandate and ensure top-down embedding
According to the GFCE Global Good Practice – National Computer Security Incident Response Teams (CSIRTs), the effectiveness of a CSIRT is determined by a mandate laid down in the national cybersecurity strategy, regulation, or law.
The national strategy should define the CSIRT’s mandate, mission, authority and responsibilities towards its constituency, stakeholders, and governance model. It is critical that there is a legal obligation to report cybersecurity incidents.
To ensure top-down embedding, a national CSIRT should have a political and governmental endorsement with well-established governance and accountability structures, as well as a connection to the national crisis management structure. The CSIRT’s connection to regional and international CSIRTs supports the mandatory coordination mechanisms between neighbouring countries as required by international protocols including the African Union Convention on Cybersecurity and Personal Data Protection.
Phase 2: Design The recommendations of this phase are aligned with the Security Incident Management Maturity Model (SIM3) in the organisation, human, tools and processes areas referenced in the model. The outcome of this phase included the approved detailed mandate, and plans covering the CSIRT services, processes, workflows organisation, skills and training structure, facilities, technologies and processes automation, cooperation, IT and information security management and detailed requirements for the implementation stage. It is good practice to publish the resulting design structure in the format provided in Request for Comments (RFC) 2350: Expectations for Computer Security Incident Response.
Phase 3: Implementation The outcomes of this phase include an approved and implemented organizational structure, hiring and training of staff, implementation of process and procedures, signed agreements with the constituency, stakeholders and partners and the CSIRT launch communication and celebrations. It is expected that at end of the implementation phase, the CSIRT is ready to deliver services to its constituency and start the operations phase.
Phase 4: Operation– At this phase, a CSIRT delivers the CSIRT services in accordance with its mandate on a daily basis. The outcomes of this phase are measured Key Performance Indicators (KPIs) for management and governance purposes and quality monitoring, annual operations performance review, annual stakeholder needs review, approval annual budget and collection of requirements for improvement.
Good practice: Annual CSIRT stakeholder workshop or meeting
An annual workshop or meeting with CSIRT stakeholders where the performance of the CSIRT and stakeholders’ priorities for and expectations of the CSIRT are presented is identified as a good practice.
Phase 5: Improvement – The outcomes of this phase include a list of improvement initiatives, the associated requirements and a preliminary budget. The improvement initiatives may arise from the operations phase; a high-level roadmap; from stakeholders; or from the management’s demand to improve the maturity and capability of the CSIRT based on frameworks such as the Security Incident Management Maturity Model (SIM3) and the Security Operation Centre Capability and Maturity Model (SOC-CMM).
Source: ENISA
There are training designed for managers and project leaders who have been tasked with implementing a computer security incident response team (CSIRT) is available. This includes the CMU-SEI Creating a Computer Security Incident Response Team and the Managing Computer Security Incident Response Teams support managers in improving the effectiveness of the team.
Case study: Establishing a CSIRT in Togo
Video Interview with: CERT Togo’s Palakiyem Assih
CERT.tg is operated by Cyber Defense Africa S.A.S. (CDA), as a service delegated by the National Cybersecurity Agency (ANCy).
Resource: Establishing CSIRTs
Establishing A CSIRT: This handbook describes the process and requirements for establishing a CSIRT, along with the relevant examples.
Handbook for Computer Security Incident Response Teams (CSIRTs) provides a description of different organisational models for implementing incident handling capabilities.


1